Hello, my name is Milad. This is my first writeup in this blog, and today I want to write about two vulnerabilities: XSS and Open Redirect, that I found on one of the banking systems. Due to confidentiality and security issues, I will redact the name of the bank.
The beginning of the stage of Wide Reconn
The scope of the project was the entire subdomains related to that bank. So, in the first step, I started using the subfinder tool and found a large number of subdomains through DNS brute force with the shuffledns tool (command below).
Subfinder -d domain -all
Shuffledns -m path-massdns -d domain.tld -w wordlist.txt -r resolver.txt
Note: I suggest using the -all switch for subfinder and, in the config file of this tool, make sure to enter the APIs of the different sites that were mentioned. (Increasing the number of results will yield better outcomes)
The beginning of the deep recon stage
After completing the Wide Recon process and finding the subdomain, I utilized the httpx tool to identify subdomains with the HTTP service enabled and examined each one based on its technology.
XSS vulnerability detection
As a result, I selected the subdomain login.redacted.ir for further investigation. Upon accessing this subdomain, my system redirected to the following path:
https://login.redacted/redacted/Sso/login/Login.aspxInitially, I encountered a login page and naturally began searching for potential vulnerabilities. However, I did not discover anything significant. Following the methodology I had developed after the Hunt class, I proceeded to use the x8 tool. With the command provided below, I attempted to locate parameters on the login page in hopes of finding something, but my efforts were unsuccessful.
x8 -w parameter-word-list.txt -u https://url -X GET POST -m 40
Then, considering that the architecture of the system was traditional or so-called Directory root-based, I started the directory and file phase so that maybe something useful could be found.
Note: In systems with modern architecture, which are so-called route-based, and the system refers the user to different sections based on pre-defined routes, phasing the directory does not work because it will not output to us until we see the complete route.
Some time passed, and I was able to find the following file:
https://login.redacted/redacted/redacted/login/Congratulation.aspx
It was a crude greeting page, and apparently, it was put there to congratulate the user if it was their employment anniversary or birthday. I said to myself that there must be a parameter here, that’s why I started Parameter Discovery again, and I was able to find a parameter called Return, which put every value it got somewhere inside the script tag, and yes, as you think, with a payload. Simple Boom!! (censored image)
Payload= milad%27-alert(1)-%27
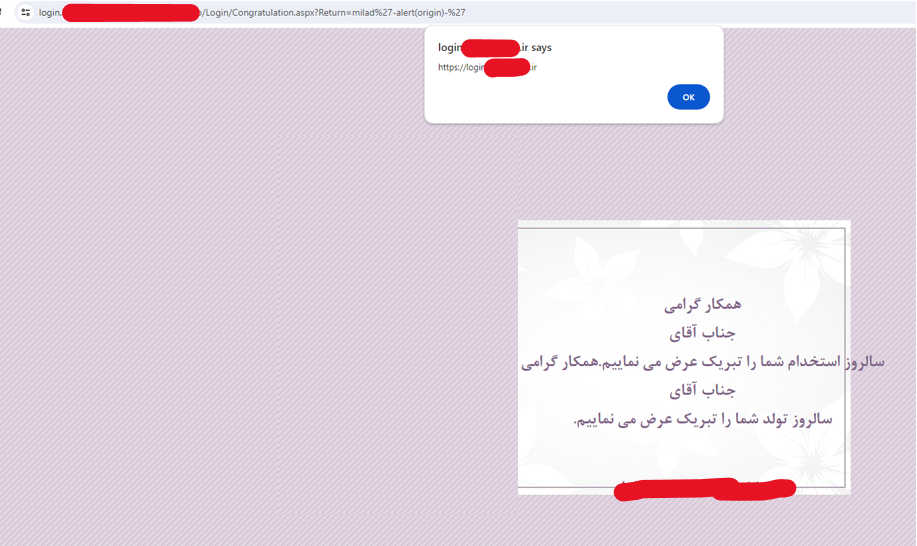
Open Redirect vulnerability detection
During the course of my investigation, I came across another file named ViewCongratulation.aspx. When a user accessed this page, they would be redirected to the user panel after a certain period of time. However, since I was not authenticated, I was redirected to the login page instead. Upon seeing the name of this page, I suspected that it might have the same parameter as the previous one. To confirm my suspicion, I checked and indeed, the parameter was present here as well. Depending on the value it received, the page would redirect the user, making it susceptible to an Open Redirect vulnerability.
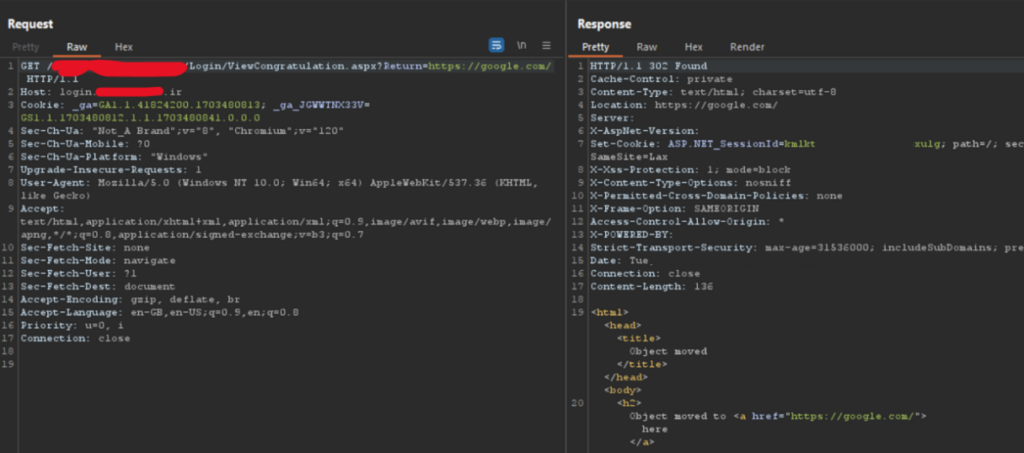
A point that I think needs attention:
• Reusing parameters on other pages
I hope you like it.
I’m not much of a writer, but my goal in writing this write-up was to let the readers know that with these simple payloads and common wordlists, vulnerabilities can be found. You just need to change your perspective on the system and look at it in a way others haven’t. From now on, I intend to share the vulnerabilities I find here with you, and at the end, give you a sentence as a gift that I’ve experienced myself.
My recommendation:
Eventually, you have to start from somewhere. Excuses like lack of resources and incomplete knowledge only hold you back… they held me back too…
